What do all the following businesses have in common?
|
|
|
You probably guessed it based on the title of this article, but they were all breached or had their businesses negatively impacted because of a third-party vendor. The list is not exhaustive, but highlights a variety of industries, including retail, financial, government, and automotive. No industry is immune.
If you do not think it is a real problem, look no further than the global outage caused by CrowdStrike. If you do not feel managing your vendors (third-party) risk is important, it is probably time to rethink your position.
In a June 2024 article, itgovernance.com posted surprising statistics related to the top 10 data breaches in the US.
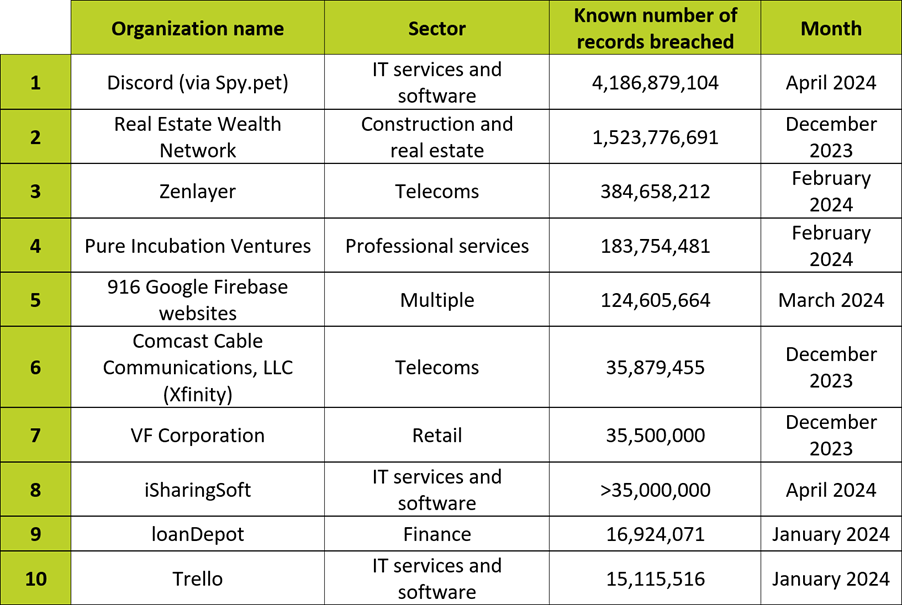
Table: Top 10 Biggest Breaches in the USA | ITGovernance.com
While all these businesses may not have been breached through a third-party, it highlights a potential risk you may face if any of these organizations are a third-party vendor for your company. Loss of intellectual property, confidential data, or strategic customer information can have a long lasting and negative impact on your business and brand reputation.
The picture I have tried to paint should be clear at this point – managing third party risk in your organization is critical to business operations. So, where do you start?
First – Compile a list of all your third-party vendors. Everyone from the office supply company to healthcare providers, contractors, software providers, and anyone outside of your organization that has physical or remote access to any of your facilities and/or systems.
Second – Define a method for classifying those vendors based on their risk to the organization. Using a simple method of classification, such as incidental or non-incidental, critical, important, or unimportant, can help define which vendors should receive the most focus.
Consider things such as:
- Are they a sole-source provider?
- Do they have access to your network?
- Do they have access to critical business systems?
- How could your business be affected if they were breached?
Third – Develop a strategy for assessing the security compliance for the respective categories. Do you send them a security questionnaire? Are there contractual obligations or penalties to meet specific security requirements?
If you find yourself struggling to identify or manage your third-party risk, we can help. IGI Cybersecurity created Vendor Secure™, a third-party risk management solution powered by Panorays and managed by IGI’s own CISO team. Want to learn more about the program and how it can benefit your organization? Contact us today for a no cost consultation.

